Authentication
Learn about the authentication strategies supported by Makerkit and how to configure them.
The Next.js/Firebase template uses Firebase Auth to manage authentication into the internal application.
The kit supports the following strategies:
- Email/Password
- oAuth Providers such as Google, Twitter, Facebook, Microsoft, Apple, etc.
- Phone Number
- Email Link
You can choose one, more, or all of them together, and you can easily tweak this using the global configuration.
By default, our SaaS Starter uses Email/Password and Google Auth.
How does Authentication work?
First, let's just take a high-level overview of how Makerkit's authentication works.
MakerKit uses SSR throughout the application, except for the marketing pages. Using SSR, we can persist the user's authentication on every page and access the user's object on the server before rendering the page.
This can help you both in terms of UX and DX. In fact, persisting the user's session server-side can help you in various scenarios:
- Simplifying the business logic: for example, checking server-side if a user can access a specific page before rendering that page
- Rendering the user's data server-side by fetching some data from Firestore in the
getServerSidePropsfunction
How does SSR work?
To enable SSR with Firebase Auth, we use Session Cookies.
- First, we use the Firebase Auth Client SDK to sign users in, as described in every tutorial. Furthermore, when a user signs in or signs up, we retrieve the ID Token and make a request to our API to create a session cookie. The session cookie remains valid for 14 days, after which it will expire.
- The cookie
sessionIdgets stored as an HTTP-only cookie: we can use this server-side for fetching the current user. - When the token expires, we sign users out of the application
So... how do they work?
- The client SDK uses the Firebase Auth credentials stored in the IndexedDB Storage. This includes interacting with Firebase Storage and Firebase Firestore on the client side.
- The server-side API uses the
sessionIdcookie to retrieve and authenticate the current user. We can then use the Firebase Admin API and interact with the various Firebase services.
Authentication Strategies
To add or tweak the authentication strategies of our application, we can update the configuration:
src/configuration.ts
auth: { // Enable MFA. You must upgrade to GCP Identity Platform to use it. // see: https://cloud.google.com/identity-platform/docs/product-comparison enableMultiFactorAuth: false, // NB: Enable the providers below in the Firebase Console // in your production project providers: { emailPassword: true, phoneNumber: false, emailLink: false, oAuth: [GoogleAuthProvider], },},Above, you can see the default configuration. It should look like the following:
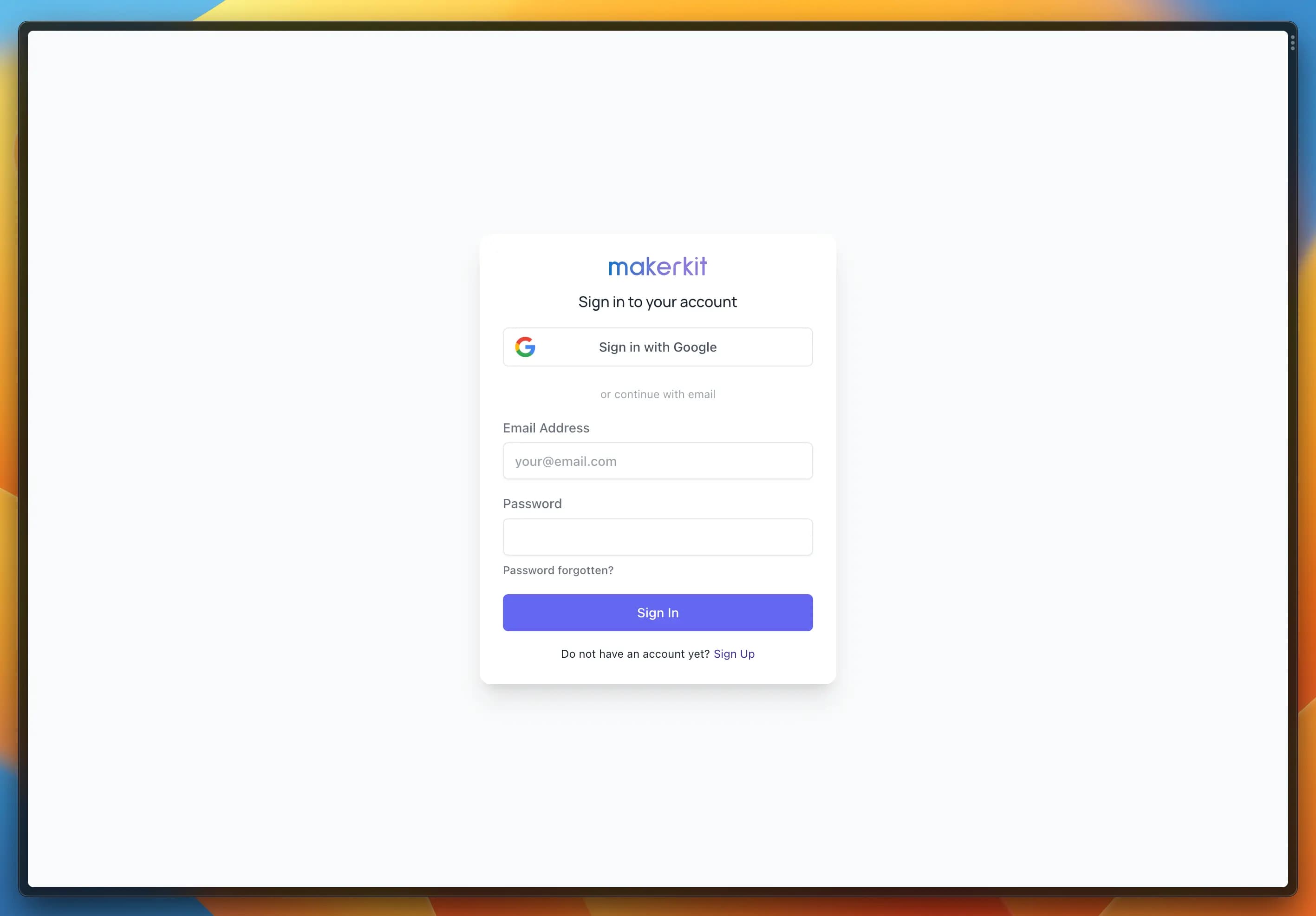
Ok, cool. But what if we wanted to swap emailPassword with emailLink and add Twitter oAuth?
We will do the following:
src/configuration.ts
import { GoogleAuthProvider, TwitterAuthProvider } from 'firebase/auth';auth: { // Enable MFA. You must upgrade to GCP Identity Platform to use it. // see: https://cloud.google.com/identity-platform/docs/product-comparison enableMultiFactorAuth: true, // When enabled, users will be required to verify their email address // before being able to access the app requireEmailVerification: process.env.NEXT_PUBLIC_REQUIRE_EMAIL_VERIFICATION === 'true', // NB: Enable the providers below in the Firebase Console // in your production project providers: { emailPassword: true, phoneNumber: false, emailLink: false, oAuth: [GoogleAuthProvider], },},And the result will be similar to the image below:
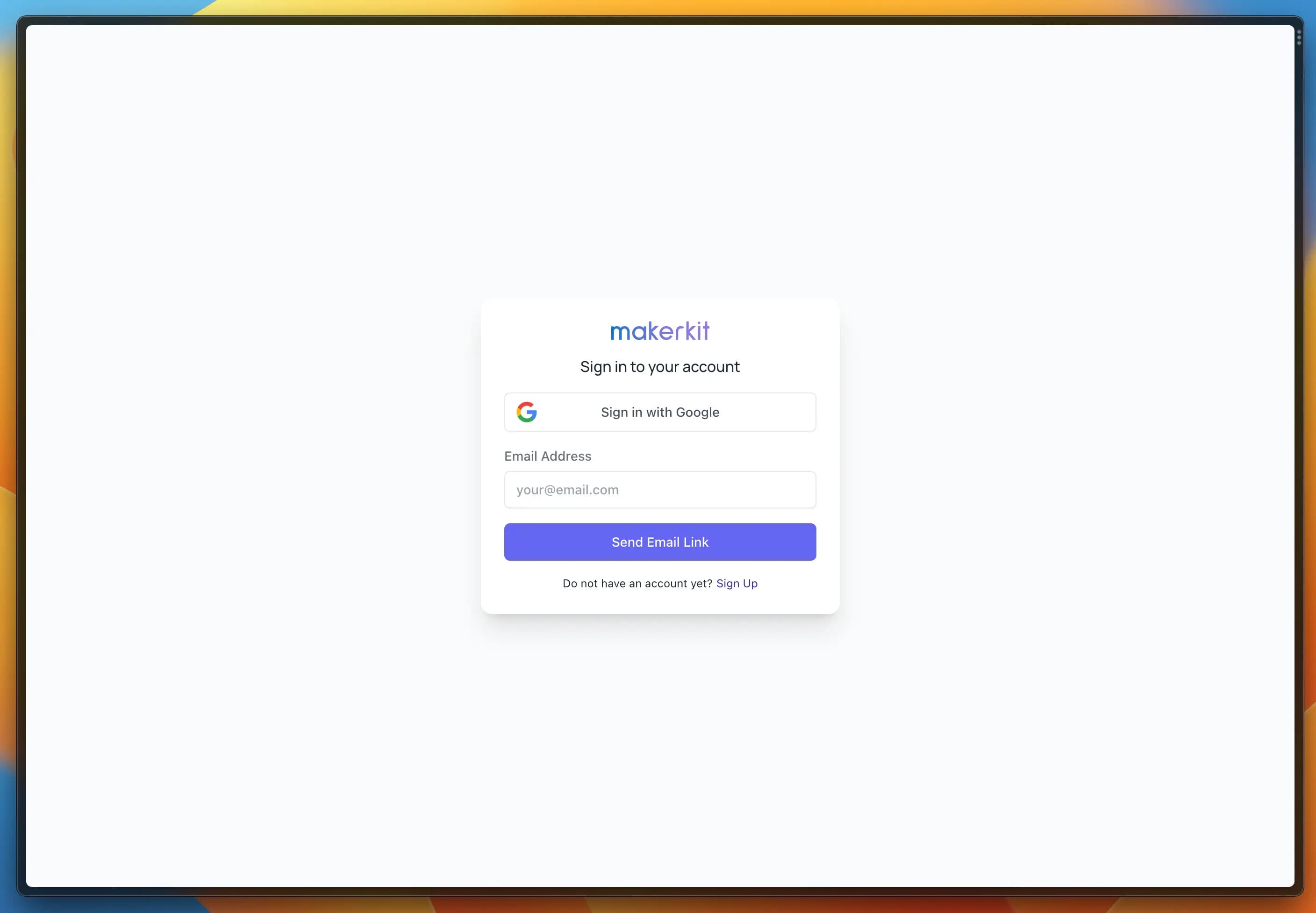
Custom oAuth providers
Additionally, we can add custom oAuth providers, such as Microsoft and Apple:
class MicrosoftAuthProvider extends OAuthProvider { constructor() { super('microsoft.com'); }}class AppleAuthProvider extends OAuthProvider { constructor() { super('apple.com'); }}Then, you will add these classes to the auth.providers.oAuth object of the configuration.
Enable the methods you want to use from the Firebase Console
Remember that you will always need to enable the authentication methods you want to use from the Firebase Console once you deploy your application to production
Creating Accounts
Users can be redirected to the Sign Up page to create an account.
Requiring Email Verification
By default, Firebase does not require users to verify their email address before being able to access the application. It is a flag on the user account, but the user is not prevented from accessing the application.
We solve this server-side by checking if the user has verified their email address before rendering the page.
To enable this feature, you can set the requireEmailVerification flag to true using the following environment variable:
.env
NEXT_PUBLIC_REQUIRE_EMAIL_VERIFICATION=true